Executive Summary
This report presents a detailed account of Chris Rock’s talk, ‘How to Overthrow a Government’, which was presented at DEFCON 24, in Las Vegas. As well being present to watch the talk in person from the front row of the conference, I watched the rebroadcast on YouTube and followed along with the slides on the DEFCON 24 DVD. For additional information, I researched Rock’s background and read interviews with him.
I also watched his presentation from DEFCON 23 on YouTube, and read a paper that he published; a hypothetical scenario that could be carried out using the material talked about in his presentation. In less than 60 minutes, Rock was able to draw a blue print on how to effectively and systematically takeover a countries critical infrastructure, implicating that countries government, and finally, incite a revolution with the aim of the government being overthrown.
All of this can carried out using traditional mercenary strategies combined with computer hacking and cyber-espionage. This report finds that implications of these ideas in action could be catastrophic to the point of real-world conflict or war, and that due to the amount of ways in which these ideas could be carried out, there is almost no way of preventing or predicting it from being attempted, and rather, that best-effort measures be in place for responding to such threats.
How to Overthrow a Government
Background Information

This 40-minute main track talk was delivered by Australian Chris Rock, founder and CEO of international cyber security and penetration testing firm, Kustodian, in what seemed to be one of the most anticipated talks of the weekend – and not just for us fellow Aussie travellers. It was 8am on Saturday morning, after some of the biggest DEFCON after parties that saw me reluctantly making my way to my first main track talk. The talk wasn’t until 10am, however with 26,000 attendees, and main track halls seating only about 2000, I made the decision to head in early and earned myself a seat in the front row for my troubles.
I wasn’t yet familiar with Rock or the talk he did at DEFCON 23, however when I saw the name and read the description of the talk, I knew that this was one I wanted to see at the conference rather than wait for the YouTube rebroadcast.
The Talk
Rock started the talk by mentioning that although he felt like the talk was a bit ‘risky’, he felt compelled to do it now due a report that came out stating that the US National Intelligence rated cyber-espionage the 2nd biggest world threat, just below ISIS (and just above North Korea). He explained that he felt like hackers (his target audience) need to reclaim the number 1 spot that they held in the years preceding, and that this talk was going to inspire us to do so, or at least scare enough politicians into reconsidering how dangerous cyber-espionage can be.
Rock explained that as well as computer hacking skills, in order to completely overthrow a government, we’d need to look at real life scenarios and tactics that have been used to overthrow governments in the past. The three ways described to overthrow a government include rigging an election, a coup d’etat, and a revolution. A coup d’etat is a seizure of a state by members of the military, or other figures high-up in a national government, where as a revolution is typically defined a takeover orchestrated by the people being governed, usually seeking a change in the way the country is being run.
It was suggested that WikiLeaks have been attempting to rig or influence the US Presidential election by targeting Democratic candidate Hilary Clinton. WikiLeaks have released incriminating emails to the public that were obtained from Clinton’s email server. This was the first an example of how cyber espionage can be used against governments – by releasing real classified documents. Rock also explained that if you’re able to hack into email servers and banks, you could also create fake emails, transactions, bribes or scandals in a smear campaign against your opposition.
Rock mentioned the ‘Mediscare’ text message that the Labor party sent out to thousands of voters in the lead up to the Australian election, warning them of the Liberal parties plan to privatise Medicare. The sender of the text message appeared as ‘Medicare’, however Labor admitted to sending out the text message without authorisation from Medicare. This is a tactic that can be used to sway voters, you just need the list of phone numbers.
However, while rigging an election may be possible in democratic nations, it’s not possible in a lot of others. So, the best way to protect your regime from election rigging, is to not have elections.
For advice on how to insight a revolution or organise a coup, Rock contacted mercenary Simon Mann. Mann is a British mercenary and former British Army officer, who was arrested and spent 5 years in prison for his involvement in the failed 2004 coup against the government of Equatorial Guinea. Rock described Mann as an expert in his field, and himself as an expert in his, and the pair worked together on how they could combine their skillsets to orchestrate a hypothetical government takeover of Kuwait.
I had to spend time researching Chris Rock and Kuwait’s politics to learn why Rock chose Kuwait as his hypothetical target, and found that Kuwait was chosen for a few reasons. For one, there are no elections for the Prime Minister in Kuwait. Instead, the Emir appoints a Prime Minister from his own family and the Prime Minister chooses the majority of his cabinet members. The rest are made up of elected members. Because of this, the Sabah family makes up much of the Kuwait government and has been in power in Kuwait since the countries establishment in 1752, and it’s likely to stay this way – unless of outside intervention.

Secondly, Chris Rock did hack into Kuwait – he was asked to by their Interior Ministry, who wished to test the Nations security measures. He was asked to look at banks, power stations, gas pipelines and other assets. Rock spent over a year putting together a presentation for the Interior Ministry, however when the Prime Minister actually did resign due to actual protests concerning actual political corruption, Rock lost all contact with the Kuwait government and claims he was never renumerated for his work.
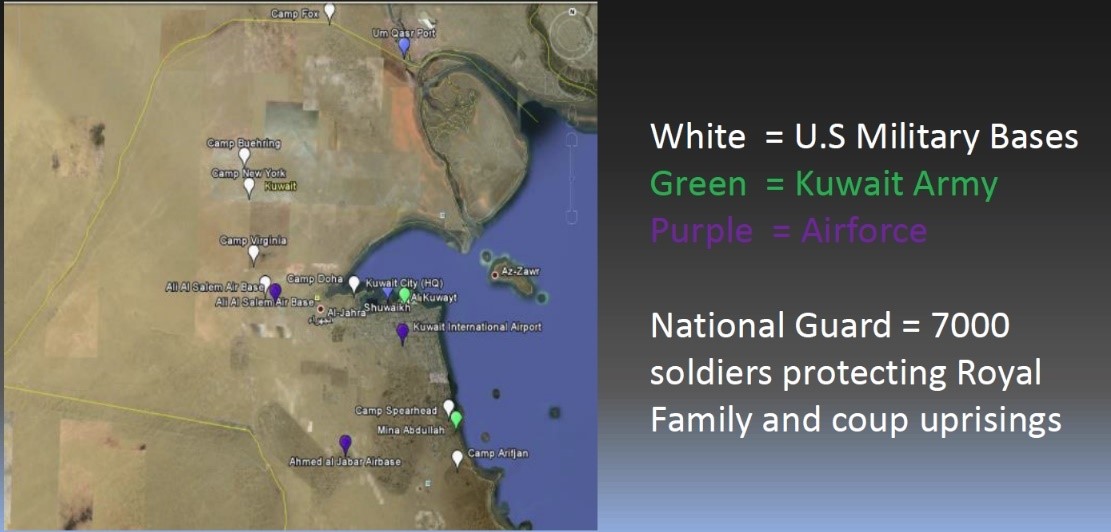
Rock went on to breakdown which of the three methods mentioned earlier he was going to use to overthrow the government. Elections we already found were no good, as they don’t apply for the Prime Minister or Head of State. The problem with pulling off a coup as an outsider in Kuwait is that not only dealing with the Kuwait’s army, there are also several US military bases and 7000 members of the National Guard who protect the Royal Family.
So, before we knew it, we’d landed on inciting a revolution. The plan was to create illusions of corruption, disrupt the population, and cause confusion within the government to destabilize it to the point where the people of Kuwait have had enough.
Rock suggested that we needed a thoughtfully planned structure of mercenary hackers. Mercenaries, we were told, were perfect as they are loyal to your cause so long as you pay them. We were also informed we needed to map out all the targets we could hack, then suggested we just hack all of them.
“I just hack them all, so I have the options of which levers I want to pull” – Chris Rock
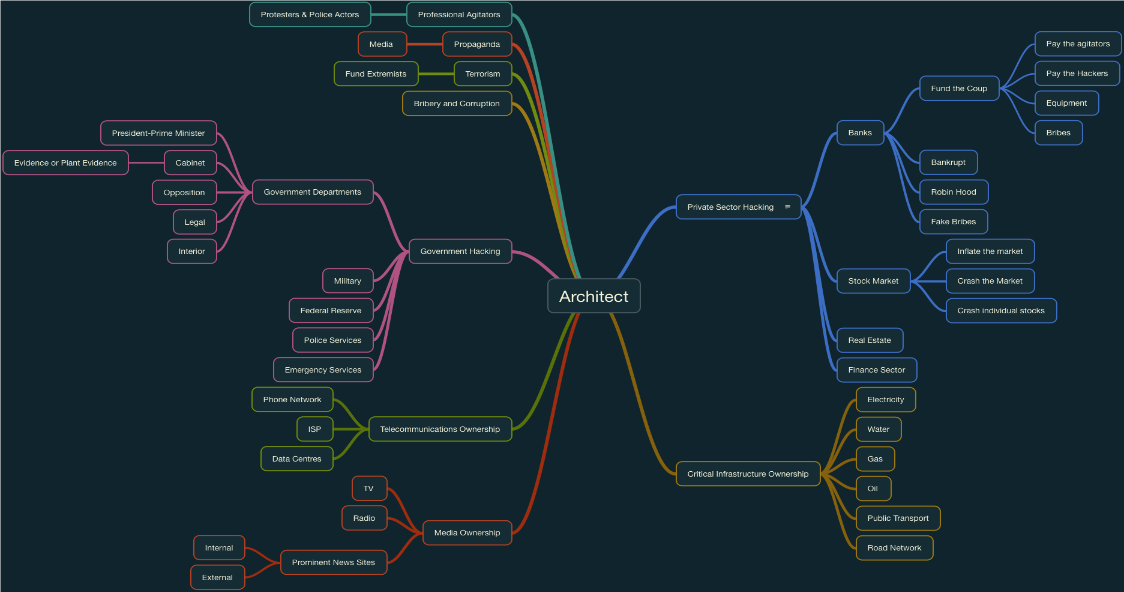
Figure 5 – Map of all our targets. Source: Chris Rock’s presentation
Next, Rock demonstrated how we would go about hacking Kuwait, and how it would help achieve our cause.
Banks were the first item discussed, because as well as being able to pay off our mercenaries, we can also move money around to implicate our targets of corruption – such as making payments to terrorist organisations and then ‘leaking’ the transactions to the public. To hack into the banks, Rock said we could either pay a cleaner, who make on average $150 a week, $2000 (that we’ll get from robbing the bank) to plant a device such as a Raspberry Pi, LAN Turtle or a NAS box on the network. These devices, of course, were available down the hall at the DEFCON merchant hall.

Figure 6 – Kuwait’s Central Bank, and the devices we can plant in them to own them. Source: Chris Rock’s presentation.
Rock’s slides then showed a series of actual screen grabs of back ends to the various banks his team were able to hack into, and explained that we could now move Government money into private or offshore bank accounts to further implicate our subjects. While we’re at it, we can also hack into the stock market and crash it as well to really annoy the citizens of Kuwait – as now their money is under fire as well.
So, now that we’ve caused some damage, we probably want to listen in on the government to see if they’re onto us – so we’ll have to hack the government. Rock demonstrated live shots of hacked government departments.
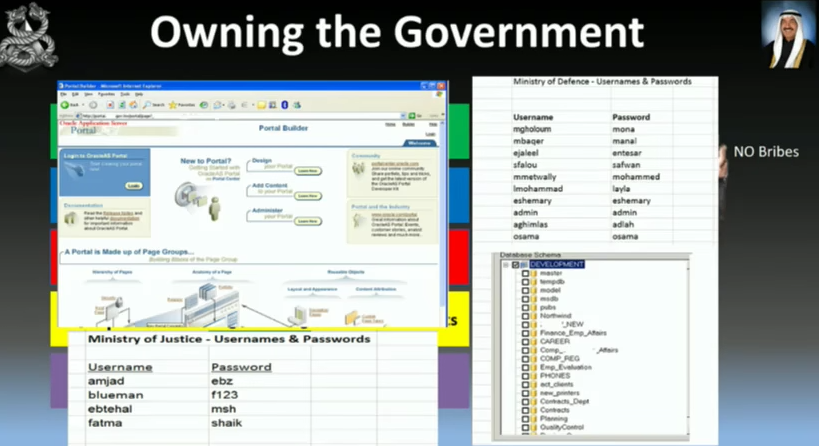
Figure 7 – Live shots showing hacked government departments. Source: Chris Rock’s presentation.
While penetration testing Kuwait, Chris Rocks team also hacked into the country’s largest ISP, Zajil. Rock explained this as a crucial step as we try to incite a revolution. This is because ISP’s these days provide cloud storage and host media content – so you’ll be able to stream your own media. You could even shut the internet down at the right time, such as if the Kuwait government was trying to inform every one of the hacks. Essentially, you will control the flow of information.
“If you own the ISP, you own the country” – Chris Rock
Next on the agenda was to disrupt Kuwait’s critical infrastructure. This includes water, power, gas, and oil. Mapping out all the power plants and sub stations is trivial – there are websites that do it for you.
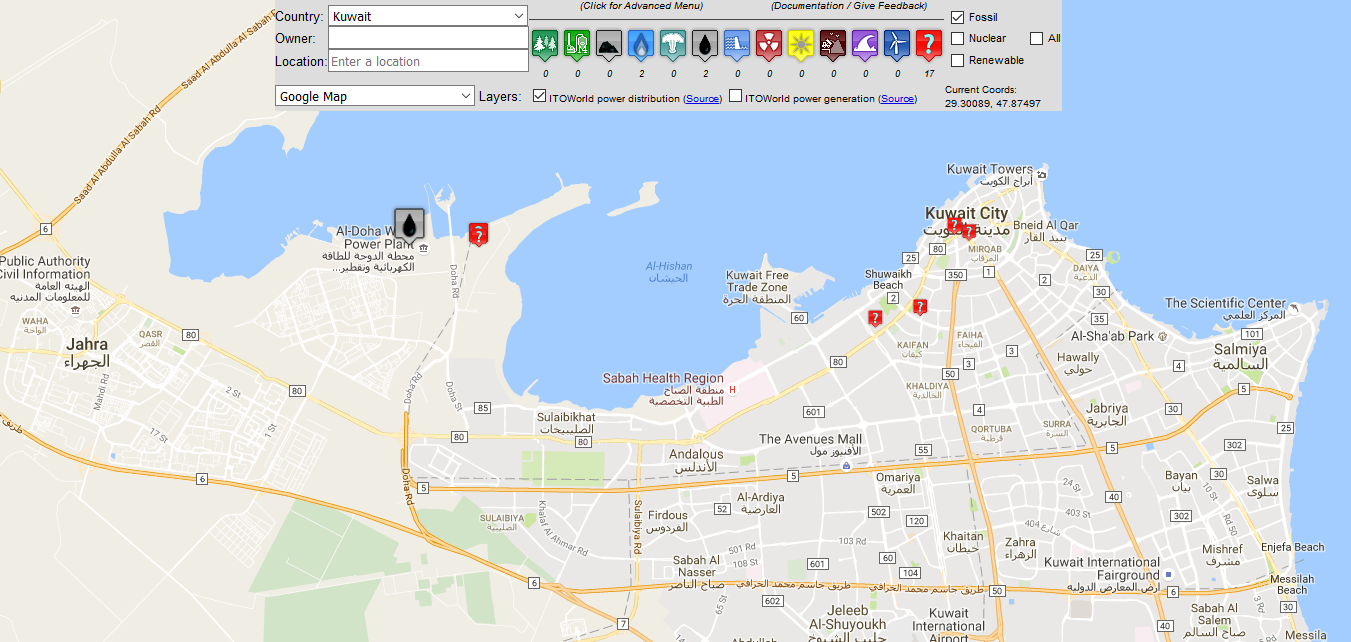
Figure 8 – Map of Kuwait showing oil plants and other infrastructure. Source: Chris Rock’s presentation.
No one likes having their air-conditioning and water cut off – especially not when you live in Kuwait City; averaging 46 °C during the summer. In fact, Kuwait broke the world record for the hottest day ever in July this year, reaching a staggering 54 °C. Obviously, ensuring the stability of water and power to millions of Kuwait citizens is paramount, and failing to do so is sure to turn the people against you. In his presentation, Rock revealed that during his real penetration testing, he found that operators use VNC – which is widely considered to be insecure – to connect to monitoring stations to control the instruments that power the country. And, if you fail to hack into the power plant, you can always use drones. Rock built and demonstrated a makeshift powerline-severer, using part of a bike frame, two 8 inch circular blades, a cordless drill and a remote control aerial drone. He then showed a video of ‘Mr Choppy’ cutting through powerlines.

Figure 9 – Mr Choppy. Source: Chris Rock’s presentation.
Now that we own everything, and can send the country in disarray at any given moment, Rock said we need to reverse engineer the media to implicate the government and kick start the revolution. To do this, Rock gave us some options for getting the media to run with a story. The ‘two source’ rule says that you need at least two sources to make a story. So, we can publish fake eyewitness testimonies or fake leaks, or, just send in stories to news outlets who already have a certain angle and they’ll publish it anyway. We could also create our own fake news websites or take control of the websites we pawned when we hacked the ISP.
Rock ended his presentation with a short video dramatizing a hypothetical scenario where hackers were able to overthrow the Kuwait Prime Minister, Nasser Al-Sabah. The video combined live shots of his actual pen-testing operation, including hacking into ISP’s, banks, and infrastructure, with an imaginary plot of planting fake news stories and moving money around to implicate Al-Sabah. The video ended with real footage of a protest calling for Sabah to resign over alleged corruption – which he did. With that, Rock called on hackers to thing bigger, combine our resources, think outside the box, and finally, reclaim that number one spot on the UN’s list of the world’s biggest threats.
Implications of the Idea
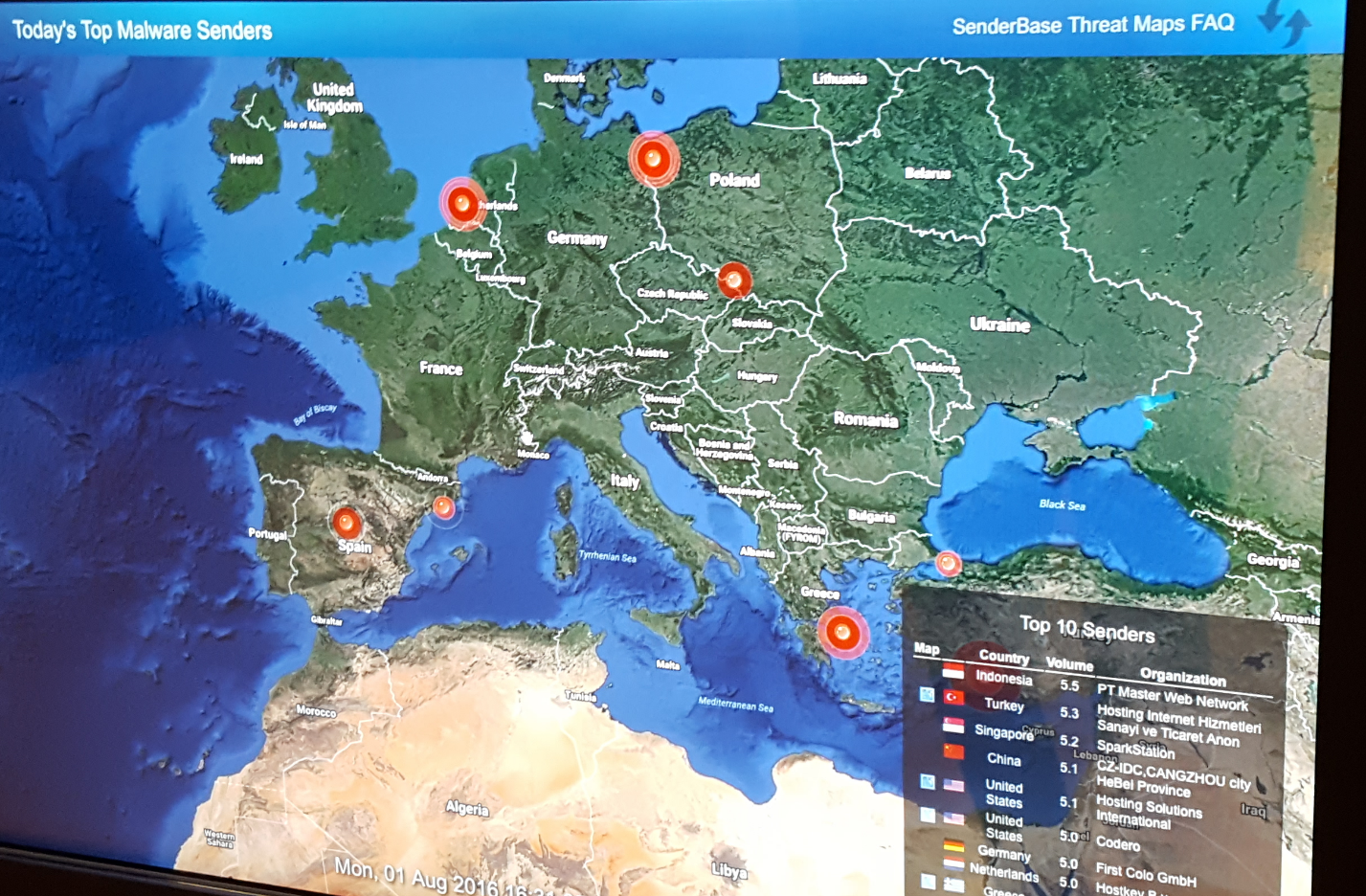
Obviously, the implications of overthrowing a government, for better or for worse, are unrivalled – and when you take the time to think about the idea, you may even come to realise that it’s not entirely far-fetched. While at Cisco Systems in Silicon Valley, we learned that a lot of malicious cyber activity is state sponsored, and their threat maps even showed a dip in malicious activity during the top contending countries’ lunch hour. Governments around the world have set up cyber-intelligence agencies that have access to virtually unlimited computing power and, both legally and not-so-legally, can gain access to ISP records, social media accounts and data centres.
Included on the DEFCON 24 DVD, is a paper by both Chris Rock and Simon Mann, titled ‘A Coup d’etat by a Group of Mercenary Hackers’. In what reads like a pitch for a Tom Clancy or Robert Ludlum novel, Mann and Rock imagine a scenario where Russia wishes to establish herself in the Gulf:
“In order to avoid being encircled by foreign powers and possible enemies Russia has long sought to establish herself as a Major Power in the Arabian Gulf and the Indian Ocean. This intent has all the more force when one considers the economic importance of the Gulf to our rivals, the USA and allies, as well as the strategic importance of the Indian Ocean.”
The paper goes on to outline a plan on how Russia will take advantage of existing tensions and alliances between countries in the Middle East, planting agents in each of them, gaining their trust, and over time, gaining access to critical infrastructure using the ideas from Rock’s presentation, in order to plant stories, implicate governments, and eventually turn Kuwait’s neighbours, Saudi Arabia, Iran and Iran against Kuwait. The end game is for Kuwait to invite Russia in for assistance, and once she is in, she has taken Kuwait without their government even knowing:
“Not to take Kuwait in the old fashioned sense … NO invasion … NO traditional Coup … instead they decide to take Kuwait by means of a creeping Coup that replaces the machinery of state – what an FSB / KGB Officer would call the apparat – with a cardre of infiltrated apparatchiks … a group who surround the throne so closely that in effect they tell the throne Do this …Don’t do that”
This is one example of how governments may use the concepts presented in the presentation. There are also the dangers that come from cutting off power and water. Rock mentioned this as a tactic for ‘annoying’ citizens to try and turn them against their government, however the real-life implications are far worse – if people are denied access to running water, or hospitals are cut off from power, the results could be fatal.
At the end of it all, the people that are most effected become the citizens of all the countries involved. It’s unlikely that a drastic change in government will come without violence, conflict and war – and then there is no guarantee that those who overthrew the government had the best intentions for that countries citizens.
Possible Mitigation Strategies
Chris Rock presented an interesting concept – the concept of inciting a revolution using computer hacking and cyber-espionage. Some of the ideas presented have always been possible in one way or another, such as faking news stories and using propaganda to sway public opinion, and others are only becoming possible now as we enter the age of the Internet of Things, with critical infrastructure now becoming prone to the kind of attacks that anything else that is accessible over a network are prone to. As such, he did not outline a step-by-step method of attacking each individual system, and every scenario is going to be different, depending on the systems you’re trying to gain access to, the tools at your disposal, and what you’re trying to achieve – amongst other variables – and therefore it’s a powerful idea.
It demonstrates that given motive, which could range from citizens or individual citizens of a nation dissatisfied with their government, to outsider interests, there are such a vast amount of attack vectors that it’s essentially impossible to be proactively mitigate all attacks. However, all best security and availability practises should be deployed, such as firewalls, encryption, monitoring and redundancy. It may be worth investigating ways to take all the critical infrastructure offline (but still functional) to prevent from unauthorised remote access.
Also, don’t hire a foreign penetration tester and ask him to hack into all your critical infrastructure and government departments without having him sign a non-disclosure agreement, and then not pay him. It could result in a presentation to hundreds and thousands of hackers about how to overthrow your government.
Related Concepts for Further Exploration
This was not the first talk Rock has done that focused more on the implications of the hack rather than the hack itself. In his DEFCON 23 his talk, titled ‘I will kill you’, Rock explains how, after spending a year researching the birth and death industry, he could gain access to online government birth and death registers for multiple countries, posing as doctors and funeral directors, and using publicly available information and social engineering. He was able to produce a death certificate for Jeff Moss, the founder of DEFCON. Rock officered some practical uses for exploiting vulnerabilities in these systems, such as revenge, insurance fraud, and setting up shell accounts. He published a book on his research titled ‘The Baby Harvest’.
Conclusion
Using mercenary strategies and planning with computer hacking and cyber-espionage is an effective way to overthrow a government. You can use the same types of hacks and attacks that are already widely used and documented, and combine them together to achieve your goal. Governments are already engaging cyber-warfare, and could use this idea practically when trying to establish control in another state. The implications of such ideas in action are likely be catastrophic, resulting in death, conflicts and wars.
Resources
- Baldwin, R. (2016). How to hack a government. [online] Engadget. Available at: https://www.engadget.com/2016/08/09/hack-governments-chris-rock-def-con-2016/ [Accessed 14 Oct. 2016].
- En.wikipedia.org. (2016). Hillary Clinton email controversy. [online] Available at: https://en.wikipedia.org/wiki/Hillary_Clinton_email_controversy [Accessed 14 Oct. 2016].
- BBC News. (2016). Kuwait’s prime minister resigns after protests – BBC News. [online] Available at: http://www.bbc.com/news/world-middle-east-15931526 [Accessed 14 Oct. 2016].
- Leo, B. (2016). The world’s hottest day EVER is recorded in Kuwait as temperature soar to a staggering 54C. [online] The Sun. Available at: https://www.thesun.co.uk/news/1492144/the-worlds-hottest-day-ever-is-recorded-in-kuwait-as-temperature-soar-to-a-staggering-54c/ [Accessed 14 Oct. 2016].
- McIlroy, T. (2016). Police won’t take action against election day ‘Medicare’ text messages. [online] The Sydney Morning Herald. Available at: http://www.smh.com.au/federal-politics/political-news/no-police-action-on-queensland-labor-party-election-day-medicare-text-messages-20160802-gqjanw.html [Accessed 16 Oct. 2016].
- Osborn, L. (2016). Hottest Cities in the World – Current Results. [online] Currentresults.com. Available at: https://www.currentresults.com/Weather-Extremes/hottest-cities-in-the-world.php [Accessed 15 Oct. 2016].
- Qazvini, M. (2016). Wikileaks Publishes 1,000 Clinton Emails. But Where Did They Get Them?. [online] Daily Wire. Available at: http://www.dailywire.com/news/7210/wikileaks-publishes-1000-clinton-emails-where-did-michael-qazvini [Accessed 19 Oct. 2016].
- Rock, C. (2016). DEF CON 23 – Chris Rock – I Will Kill You. [online] YouTube. Available at: https://www.youtube.com/watch?v=9FdHq3WfJgs [Accessed 16 Oct. 2016].
- Rock, C. (2016). DEF CON 24 – Chris Rock – How to Overthrow a Government. [online] YouTube. Available at: https://www.youtube.com/watch?v=m1lhGqNCZlA [Accessed 14 Oct. 2016].
Rock, C. and Mann, S. (2016). A COUP D’ETAT BY A GROUP OF MERCENARY HACKERS. [online] Available at: https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEFCON-24-Chris-Rock-How-to-overthrow-a-Government-Kuwait-Coup-WP.pdf [Accessed 18 Oct. 2016].
- Simone, A. (2016). Q&A: Meet the hacker that can overthrow a government with just a laptop. – Practically Unhackable. [online] Medium. Available at: https://medium.com/un-hackable/q-a-meet-the-hacker-that-can-overthrow-a-government-with-just-a-laptop-531a6bcc3b12#.dn40v88ap [Accessed 17 Oct. 2016].
- Sorcher, S. (2015). Lessons from a digital mercenary: Beware the ‘October Surprise’. [online] The Christian Science Monitor. Available at: http://www.csmonitor.com/World/Passcode/2016/0810/Lessons-from-a-digital-mercenary-Beware-the-October-Surprise [Accessed 15 Oct. 2016].