Executive Summary
Background
Dr has engaged NSI Higher Ed students to perform a Security Assessment on the Damn Small Linux (DSL) Linux distribution. This report details the findings and proposes recommendations to harden the distribution. Dr Gao requires that DSL maintains its small size (around 50MB), and as much of its functionality as possible.
In order to carry out the Security Assessment, all default server features of DSL were enabled and assessed:
Print Server
BetaFTP – an FTP Server
Monkey Web – a Web Server
SSH Server
Applications tested include:
Xpdf – a PDF viewer
Bash – Bourne Again Shell
Xchat – an IRC client
Bon Echo / Firefox 2.0 – a web browser
Cryptography functions used for SSH connections were also assessed.
Summary
Several open source and freely available tools were used to assess a release of an old Linux distro; Damn Small Linux 4.11rc2 (DSL). This distribution was released in 2012, and therefore, many of the applications were out of date, and had known vulnerabilities – some dating as far back as 2002. The NIST vulnerable scoring system was used to rate each vulnerability, with an average score of High, meaning that DSL is terribly insecure in its current state. Recommendations to secure this distro include disabling weak cryptography functions, updating applications, or using different applications all together. Effort was made to keep DSL as close to its original size as possible (50 MB).
Methodology
Vulnerabilities are discovered using freely available tools and services, and assessed by consulting online vulnerability databases. Each vulnerability is scored based on the NIST CVSS v.3.0 Ratings: https://nvd.nist.gov/vuln-metrics/cvss
CVSS v3.0 Ratings
|
| Severity |
Base Score Range |
| Low |
0.0-3.9 |
| Medium |
4.0-6.9 |
| High |
7.0-8.9 |
| Critical |
9.0-10.0 |
Engagement Details
Scanner Details and Tool Set
Scanners
Nessus
Browserscope
Tools
Kali Linux
Nmap 7.60
List of Targets
| Hostname |
Operating System |
IP Address |
| DSL |
Damn Small Linux |
192.168.0.110 |
Vulnerabilities
Applications
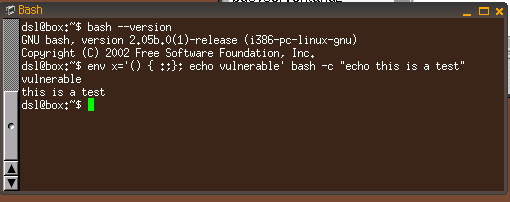
Bash Remote Code Execution (Shellshock)
|
| Impact |
CVSS Score 10.0 |
| Type |
Command Injection |
| Evidence |
 |
| Description |
The remote host is running a version of Bash that is vulnerable to command injection via environment variable manipulation. Depending on the configuration of the system, an attacker could remotely execute arbitrary code. |
| Recommendation |
Update Bash to the latest version. |
| Consequence of Recommendation |
| Size |
Unchanged |
There are no differences to size if Bash is updated, |
| Functionality |
Unchanged |
There are no differences to the functionality if Bash is updated. |
| Security |
More Secure |
Updating Bash to the latest version will make DSL more secure. |
|
| Sources |
http://seclists.org/oss-sec/2014/q3/650
http://www.nessus.org/u?dacf7829
https://www.invisiblethreat.ca/post/shellshock/ |
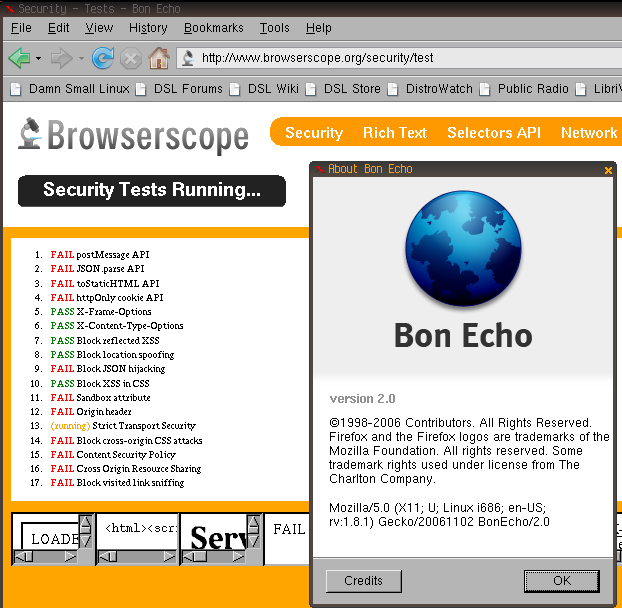
Legacy Web Browser
|
| Impact |
No CVSS score – Determined to be 10.0 |
| Type |
Multiple Security Flaws / |
| Evidence |
 |
| Description |
Damn Small Linux comes bundled with Bon Echo – the development name of Firefox 2.0, released in 2006. This web browser has many security flaws and is unable to view many modern websites. |
| Recommendation |
Update to the latest version of Firefox or use another modern browser. |
| Consequence of Recommendation |
| Size |
Increased size |
The installation file for Firefox 2.0 is 5.63MB. The current version of Firefox when installed on Windows is 118 MB. Depending on the requirements, other lightweight web browsers could be used instead to reduce size. |
| Functionality |
More functionality |
An up to date browser is able to view modern websites and install current add-on |
| Security |
More Secure |
An up to date browser will receive security updates |
|
| Sources |
http://www.browserscope.org/security/test
http://www.oldapps.com/firefox.php?old_firefox=26#download-section |
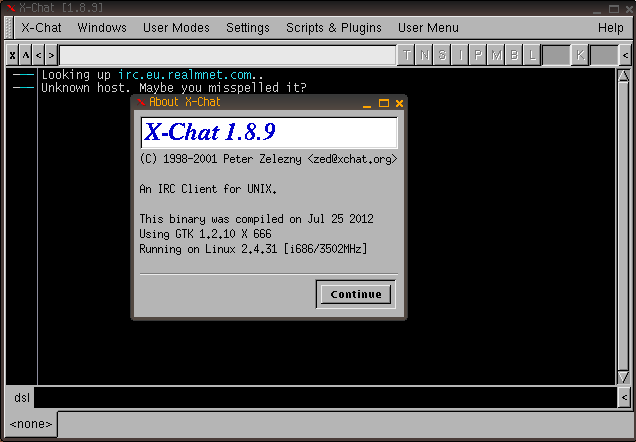
XChat 1.8.9
|
| Impact |
CVSS Score – 7.5 |
| Type |
Buffer Overflow |
| Evidence |
 |
| Description |
CVE-2004-0409
Stack-based buffer overflow in the Socks-5 proxy code for XChat 1.8.0 to 2.0.8, with socks5 traversal enabled, allows remote attackers to execute arbitrary code.
XChat 1.8.9 was released in the early 2000’s, and the latest version, 2.8.9, was released in August 2010. Support has since been discontinued. |
| Recommendation |
Remove and replace with HexChat – an opensource and free fork of XChat. HexChat is still supported as of October 2016. |
| Consequence of Recommendation |
| Size |
Unchanged |
The installation files for the latest versions of both XChat and HexChat are 1.4MB. |
| Functionality |
Additional functionality |
HexChat has additional functionality. |
| Security |
More secure |
HexChat fixes security issues that are present in Xchat. |
|
| Sources |
http://www.cvedetails.com/cve/CVE-2004-0409/
https://hexchat.github.io/news/announcement.htmlhttps://www.slant.co/versus/4192/4382/~hexchat_vs_xchat |
Xpdf
|
| Impact |
CVSS Score 9.3 |
| Type |
Buffer Overflow |
| Evidence |
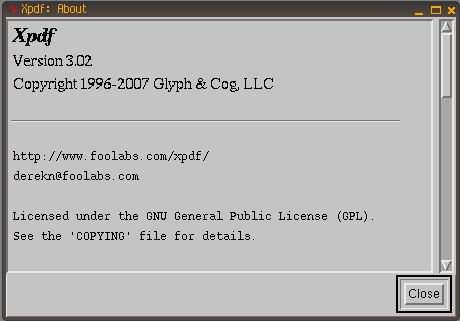 |
| Description |
Integer overflow in the ObjectStream::ObjectStream function in XRef.cc in Xpdf 3.x before 3.02pl4 and Poppler before 0.12.1, as used in GPdf, kdegraphics KPDF, CUPS pdftops, and teTeX, might allow remote attackers to execute arbitrary code via a crafted PDF document that triggers a heap-based buffer overflow. |
| Recommendation |
Upgrade Xpdf to the latest version. The latest version as of this report is 4.00, released August 10, 2017. |
| Consequence of Recommendation |
| Size |
Unchanged |
There are no differences to size if Xpdf is updated. |
| Functionality |
Unchanged |
There are no differences to the functionality if Xpdf is updated. |
| Security |
More secure |
The latest version of Xpdf addresses security issues present in version 3.02. |
|
| Sources |
https://www.cvedetails.com/cve/CVE-2009-3608/ |
OpenSSH 3.6.1p2
|
| Impact |
CVSS Score 9.3 |
| Type |
Denial of Service Execute Code |
| Evidence |
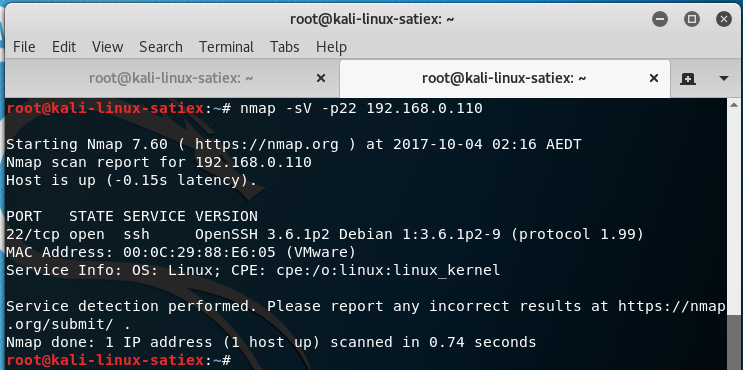 |
| Description |
Signal handler race condition in OpenSSH before 4.4 allows remote attackers to cause a denial of service (crash), and possibly execute arbitrary code if GSSAPI authentication is enabled, via unspecified vectors that lead to a double-free. |
| Recommendation |
Update OpenSSH to the latest version, 7.5 as of this report: https://www.openssh.com/ |
| Consequence of Recommendation |
| Size |
Unchanged |
There are no differences in size if OpenSSH is updated. |
| Functionality |
Unchanged |
There are no differences in functionality if OpenSSH is updated. |
| Security |
Increased |
OpenSSH 7.5 addresses security vulnerabilities present in OpenSSH 3.6.1p2. |
|
| Sources |
https://www.cvedetails.com/cve/CVE-2006-5051/ |
Cryptography
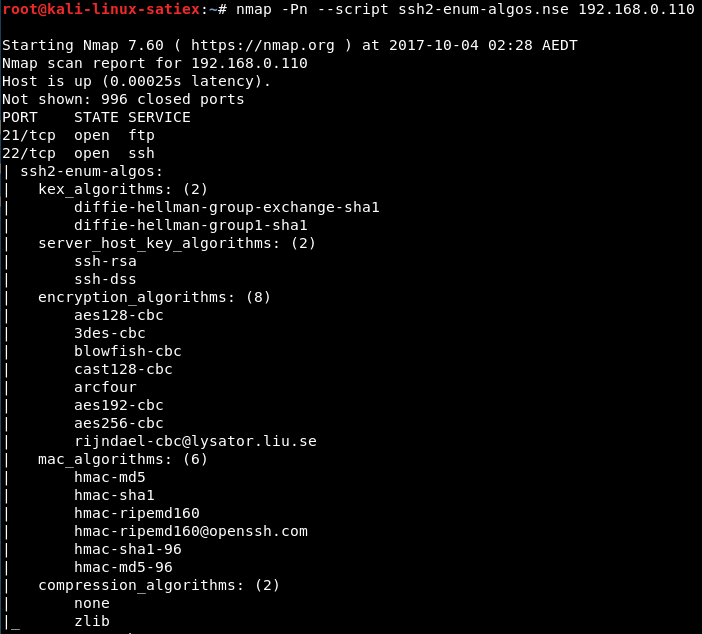
SSH Weak Algorithms Supported
|
| Impact |
CVSS Score 4.3 |
| Type |
Weak Cryptography |
| Evidence |
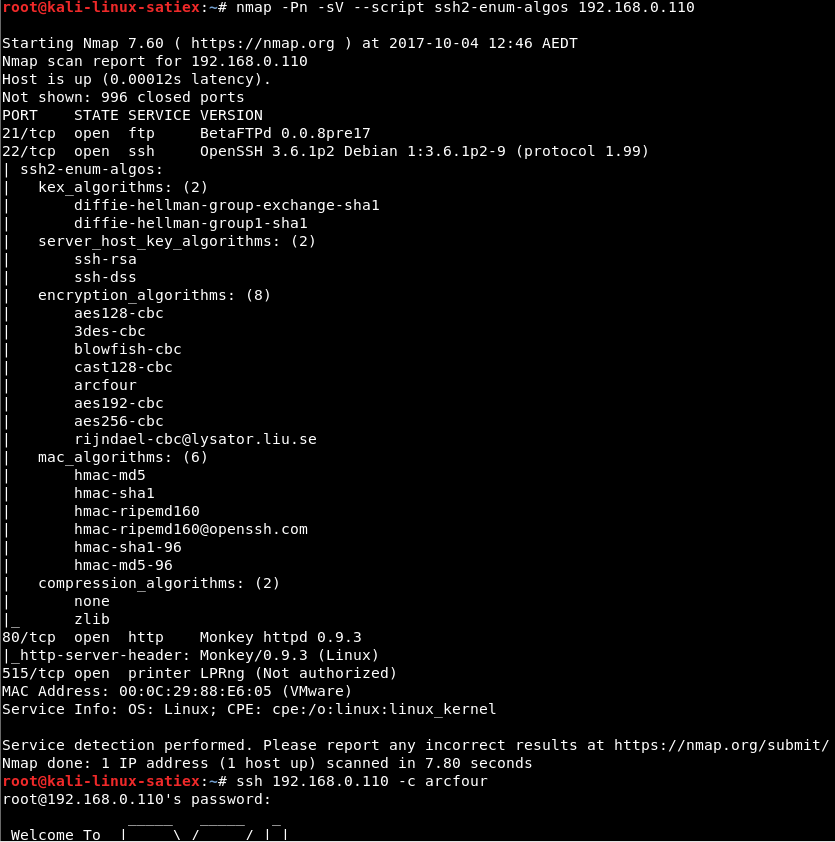 |
| Description |
Nessus has detected that the remote SSH server is configured to use the Arcfour stream cipher or no cipher at all. RFC 4253 advises against using Arcfour due to an issue with weak keys. |
| Recommendation |
Remove weak ciphers by editing the /etc/ssh/sshd_config file: http://www.accella.net/knowledgebase/ask-the-sysadmin-fixing-cipher-and-mac-ssh-security-problems/ |
| Consequence of Recommendation |
| Size |
Unchanged |
Changing the sshd_config file won’t make any difference to the size of DSL. |
| Functionality |
Decreased functionality |
Arcfour ciphers can no longer be used |
| Security |
Increased security |
Weak Arcfour ciphers can no longer be used to create or join SSH sessions |
|
| Sources |
https://tools.ietf.org/html/rfc4253#section-6.3 |
Resources
Behnke, A. (2017). Ask the SysAdmin: Fixing Cipher and MAC SSH Security Problems | Accella. [online] Accella.net. Available at: http://www.accella.net/knowledgebase/ask-the-sysadmin-fixing-cipher-and-mac-ssh-security-problems/ [Accessed 3 Oct. 2017].
Linux.uits.uconn.edu. (2014). SSH – weak ciphers and mac algorithms | UITS Linux Team. [online] Available at: http://linux.uits.uconn.edu/2014/06/25/ssh-weak-ciphers-and-mac-algorithms/ [Accessed 3 Oct. 2017].
Hewlett Packard Enterprise Community. (2015). Disable CBC mode cipher encryption , MD5 and 96-bit MAC algorithms. [online] Available at: https://community.hpe.com/t5/Security/Disable-CBC-mode-cipher-encryption-MD5-and-96-bit-MAC-algorithms/td-p/6691343 [Accessed 2 Oct. 2017].
Cvedetails.com. (2006). CVE-2006-5051 : Signal handler race condition in OpenSSH before 4.4 allows remote attackers to cause a denial of service (crash), and po. [online] Available at: https://www.cvedetails.com/cve/CVE-2006-5051/ [Accessed 4 Oct. 2017].
Weimer, F. (2014). oss-sec: Re: CVE-2014-6271: remote code execution through bash. [online] Seclists.org. Available at: http://seclists.org/oss-sec/2014/q3/650 [Accessed 4 Oct. 2017].
Nessus.org. (2014). Bash specially-crafted environment variables code injection attack – Red Hat Customer Portal. [online] Available at: http://www.nessus.org/u?dacf7829 [Accessed 4 Oct. 2017].
Invisible Threat. (2014). Shellshock – CVE-2014-6271 · Invisible Threat. [online] Available at: https://www.invisiblethreat.ca/post/shellshock/ [Accessed 4 Oct. 2017].
Cvedetails.com. (2004). CVE-2004-0409 : Stack-based buffer overflow in the Socks-5 proxy code for XChat 1.8.0 to 2.0.8, with socks5 traversal enabled, allows re. [online] Available at: http://www.cvedetails.com/cve/CVE-2004-0409/ [Accessed 4 Oct. 2017].
Hexchat.github.io. (2012). Announcement – HexChat. [online] Available at: https://hexchat.github.io/news/announcement.html [Accessed 4 Oct. 2017].
Slant – HexChat vs XChat detailed comparison as of 2017. [online] Slant. Available at: https://www.slant.co/versus/4192/4382/~hexchat_vs_xchat [Accessed 4 Oct. 2017].
Browserscope.org. (n.d.). Security – Tests. [online] Available at: http://www.browserscope.org/security/test [Accessed 4 Oct. 2017].
OldApps.com. (n.d.). Old Version of Firefox 2.0 Download – OldApps.com. [online] Available at: http://www.oldapps.com/firefox.php?old_firefox=26#download-section [Accessed 4 Oct. 2017].